Beware! There is a Drastic Increase in Cyber Attacks
Never missing out on an opportunity to cash in on a crisis, criminal actors are raising the stakes on cyber-attacks. Please review the following examples and share them with your team and coworkers. The last think a business needs during this crisis is to be shut down by ransomware or a data breach.
Why are attacks on the rise?
- With an overnight change to a work-from-home workforce, traditional systems of checks and balances are compromised.
- People do not function at their best when under stress. The current quarantine has increased stress and made us more susceptible to mistakes.
- Employees are separated from their coworkers and cannot just “ask their neighbor” if they are suspicious. They are more likely to take a risk than pick up the phone or otherwise ask for guidance.
- Cyber crime is now estimated as a 3 trillion dollar a year industry. With such a strong profit opportunity, cyber-attacks have been rising exponentially over the past several years.
The following are samples or some recent phishing attempts. Examples have been provided where possible:
- Emails with attachments for a voice mail. The typical email says that there is a voice mail attached from the “xyz” phone system. The sender is hoping that you have an “xyz” phone system and will open the attachment – which is malware. Suggestion: Dial in to your voice mail and pick up the message by phone rather than rely upon email attachments.
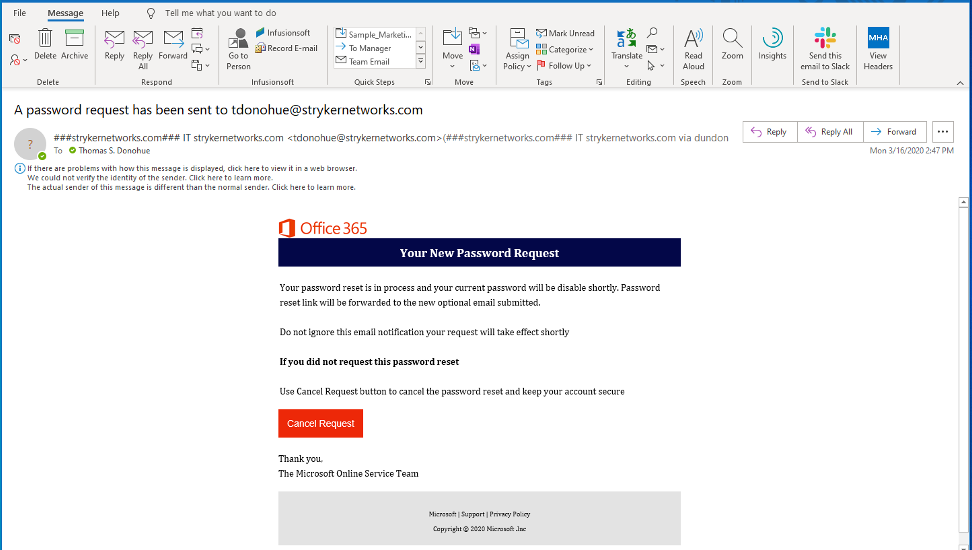
- Office 365 Password Reset Requests: You receive an email that your password reset is in process and your current password will be disabled shortly. If you did not request this then hit the button “Cancel Request”. The email looks very official and even comes from your company (or in the case of my example ###strykernetworks### IT strykernetworks ) If you “cancel the request” you have just downloaded malware or will be directed to a site that will ask for your user name and password. If you receive password resets or account closure emails that you were not expecting, submit the email to the Stryker help desk. DO NOT CLICK THE BUTTON.
- You receive an email or phone call from an officer of your company instructing you to send money. While this may be part of the new workflow, it is a great opportunity for cyber criminals. Suggestions: Put secondary confirmations in place such as a requirement for phone verification of money requests, a common pass phrase to be used to validate requests, etc. In short, do not send money unless you are positive that it is authorized from someone you know.
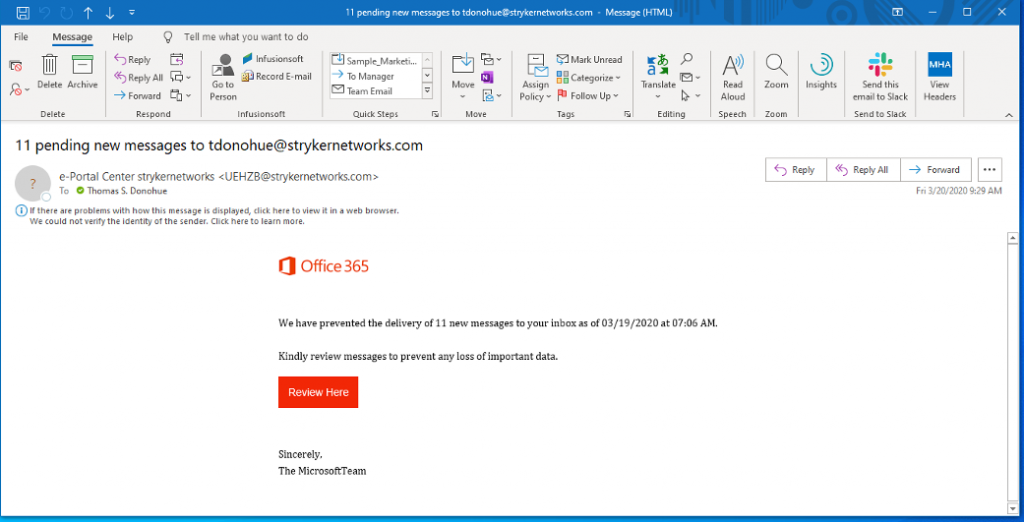
- There are pending messages for yourname@yourcompany.com. “we have prevented the delivery of 11 new messages to your inbox as of 03/19/2020 at 7:06AM. Kindly review message to prevent any loss of important data. Button: Review Here.” THIS IS NOT FROM MICROSOFT. This sample came to me from UEHZB@strykerntworks.com – if the sender seems odd and the content is unfamiliar, you are better off asking and waiting for confirmation than clicking a button and risking an attack.
- As a general rule, Stryker is avoiding email attachments for marketing material. We will be providing links to our web site (strykernetworks.com) and you can download material from there as it becomes available. This helps you to validate that the material can be trusted. Do not open attachments unless they are expected and from known entities.
What can I do to protect myself?
The best thing you can do to protect yourself is to make sure that you and your team are vigilant. Cyber criminals don’t target systems, they target people. Follow some simple guidelines:
- Be suspicious: always look at an email, especially one with an attachment or a link, as a potential threat
- Look at the email address. Does it have an odd name? Is there a misspelling?
- If it sounds too good to be true, it probably is. If you are not expecting a package from UPS, don’t be surprised if the shipping confirmation is malware.
- Is the email asking you to do something important, but you’ve never seen anything like it before? The examples above look official, but have you ever had a password reset request from Office 365? Has your boss ever emailed you to transfer funds before?
Can Stryker help protect me?
Stryker has a number of products that can help keep you protected. These include:
- Help Desk support to review suspicious emails
- Office 365 Advanced Threat Protection (ATP) to stop malware before it gets delivered to your computer.
- Anti-malware software for your Workstation or Laptop
- Comprehensive Business Continuity products to ensure that, should you be compromised, your systems can be restored from backup.
If you would like a no charge, no obligation consultation to review your options, please call us today at 847-908-3210
